Table of Contents
Over The Air Updates (OTA)
Introduction
Starting with version 1.2.0, the Wardriver is able to update itself over the air without a PC. This saves you the effort of compiling the code yourself, setting up the Arduino IDE, etc.
How To
To keep things as simple as possible, most of the required steps involve just one click. Follow these steps to update your Wardriver:
- Turn on your Wardriver as normal and then access the web interface via your network. This is described in the “Accessing Data” section of the Usage Instructions page. Ensure your Wardriver has a working internet connection such as your home WiFi.
- At the top of the main page, you should see a link stating either “A software update is ready” or “Software update available” - Click this link. Note: if the message states an update is “ready”, the following step will be skipped.
- The new update will now download, and the progress of the download will be shown on the screen of your Wardriver. Once the download completes, click the link stating “check this page once the download is complete” in the browser.
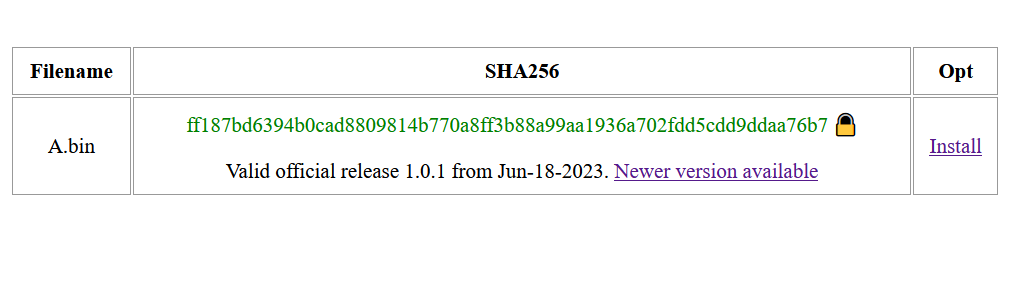
- A page will load and this can take 1-3 minutes, the Wardriver screen will show a progress indication until it loads. This page contains a table with all of the available updates, usually this is A.bin and B.bin which represent updates for the 2 separate ESP32 processors in the Wardriver.
- Click “install” on the right of the table to begin the update. You should do this for both A and B when possible. More information about this page is listed below. Avoid turning off or powering down your Wardriver during the install. The Wardriver screen will show the progress of the update.
The update page should contain a table which looks like this:
The filename simply informs you whether the update is for the “A” ESP32 or the “B” (the 2 processors within the Wardriver). Usually an update for both ESP32s will be available simultaneously but it is okay if only 1 is available. It is recommended to install both (if there are 2) on the same day so that both ESP32s will be “in sync” with their updates.
The SHA256 section shows the hash of the update so, if you wish, you can manually check it matches the hash of our release. If the hash is written in green and has a padlock next to it, this verification has been completed automatically and confirms the update is genuine and valid.
Another line will be displayed below stating the results of this verification, including the version number and release date of the update. As shown above, you may also see “Newer version available” indicating that a new update has been released since you downloaded the update(s). If you want the latest version, you should click this.
If the hash appears in red and does not include this line, it may be corrupt or tampered with. It is not recommended to install the update in this situation. This may also indicate an issue communicating with the internet, so it may resolve itself if you try again later.
Manual OTA Updating
The feature as documented above will download updates from our OTA servers which is convenient for most situations. However, if you want to run alternative software or pre-release software which is not available from the OTA server, you can upload an update manually.
To upload an update manually, follow these steps:
- Turn on your Wardriver as normal and then access the web interface via your network. This is described in the “Accessing Data” section of the Usage Instructions page. Ensure your Wardriver has a working internet connection such as your home WiFi.
- Scroll down to the very bottom of the main page. You should see an option to select a file, use this to find the update file on your PC. You should not rename these files, and they are usually called “A.ino.esp32.esp32.esp32.bin” and “B.ino.esp32.esp32.esp32.bin”.
- Press the upload button and watch the screen on your Wardriver. Your browser will automatically redirect to the correct page once the upload is complete.
- The page which loads is the same update page as listed above. If you upload a custom update, the SHA256 hash will likely be listed in red. You should manually compare this hash with the file on your PC to ensure the update is valid.
It is always possible to install updates “the old way” by using the Arduino IDE. This method is documented on the GitHub Repo.
Security Considerations
All communication with the OTA servers is encrypted making it very unlikely (almost impossible) for it to be tampered with. To ensure that your Wardriver is talking to the official server, 2 SSL certificates are installed within the Wardriver software which cryptographically proves the communication is taking place with the official server.
To help ensure a high level of security, these certificates will be replaced on occasion and the replacement certificates will be issued to your device in updates. If you go more than approximately 1 year without updating, your device will have outdated certificates and will be unable to connect to the OTA server. If this happens, you will have to update your device manually or disable the checksum verification as described below.
As of the 1.2.0b1 release, updates can only be installed if they are genuine. This extra check can be disabled using the "enforce checksums" advanced option but this exposes you to big security risks when using untrusted WiFi networks. See the Advanced Config page for instructions on how to change the advanced settings on your wardriver.
Disabling the “enforce checksums” feature will allow you to install custom or invalid updates. This can also be used to install updates when there is a problem with the OTA server, or when the SSL certificates on your device have expired. Changing this option is not recommended.
SSL Certificates
As briefly mentioned in the previous section, the wardriver firmware has 2 SSL certificates built-in. This section describes the design decision behind this idea for those curious.
Generally, the authenticity of a HTTPS connection is verified by a certificate authority who will attest a particular certificate belongs to a specific domain using some kind of identity check. This requires that all devices making HTTPS connections need to have a bundle of CA certificates installed somewhere and these need to be kept up to date.
While this is a good way to ensure the server you are connected to is the one you expected, it's not the only way. To reduce overhead, the wardriver firmware has 2 unsigned (aka “self signed”) certificates built-in, and these are sure to be genuine since they are in the offical open-source firmware. In addition, I sign my git commits so you can be very sure I am the one who put them into the firmware.
This removes the need to use a certificate authority and the need to keep a CA certificate bundle up to date on every wardriver. Only the 2 pre-installed certificates are considered valid, so if your device somehow connects to another server which has a different certificate, the connection will be prevented.
Only a single certificate will be used on the OTA server at a time and once it gets phased-out, the second certificate will be used instead. This allows the wardriver to always connect, even if a certificate gets replaced. Upon replacing a certificate, a new firmware version will be released so all wardrivers again have 2 working certificates.
Privacy Considerations
Since your Wardriver connects to our OTA servers in order to check for updates, some information about your device is sent over the internet. This information is as follows:
- Your Wardriver hardware model (eg, “rev3”)
- Your Wardriver current software version (eg, “1.2.0”, “1.2.1b1”, etc)
- The IP address of your internet connection (NOT stored)
Due to the way the internet works, your IP address is always sent to every service you connect to including the Wardriver OTA servers. The OTA servers do not log or process these IP addresses.
We store the following information for internal analytical purposes:
- Your Wardriver hardware model (eg, “rev3”)
- Your Wardriver current software version (eg, “1.2.0”, “1.2.1b1”, etc)
- The time taken for a request to complete.
- The date/time the request happened.
This information is not enough to identifiy a specific person but is very helpful to determine how well the OTA service is working and which Wardriver models and versions are more popular.
You may disable the OTA functionality to prevent this logging of information. A link will appear at the bottom of the main page stating “opt out”. You can re-enable the feature again at any time.